17 years of helping Indian businesses
choose better software
Push Security
What Is Push Security?
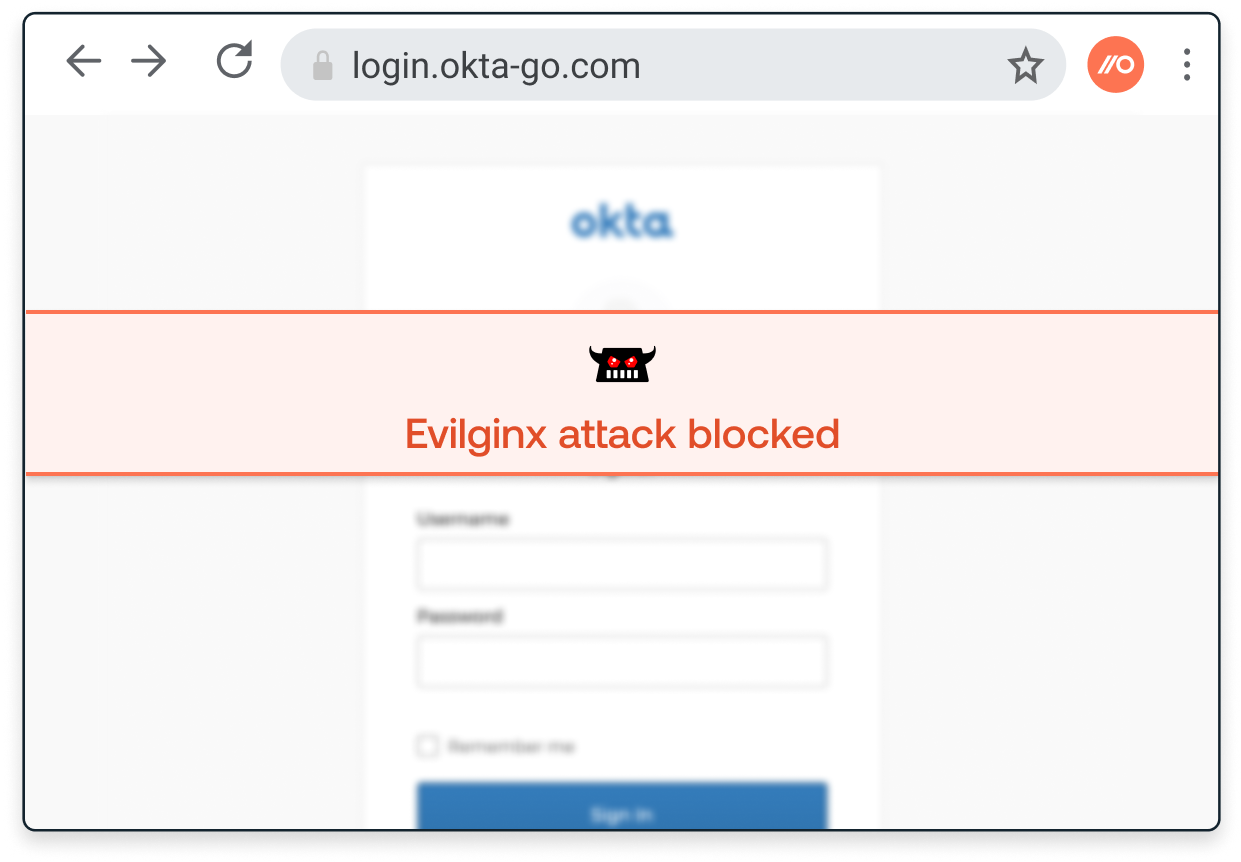
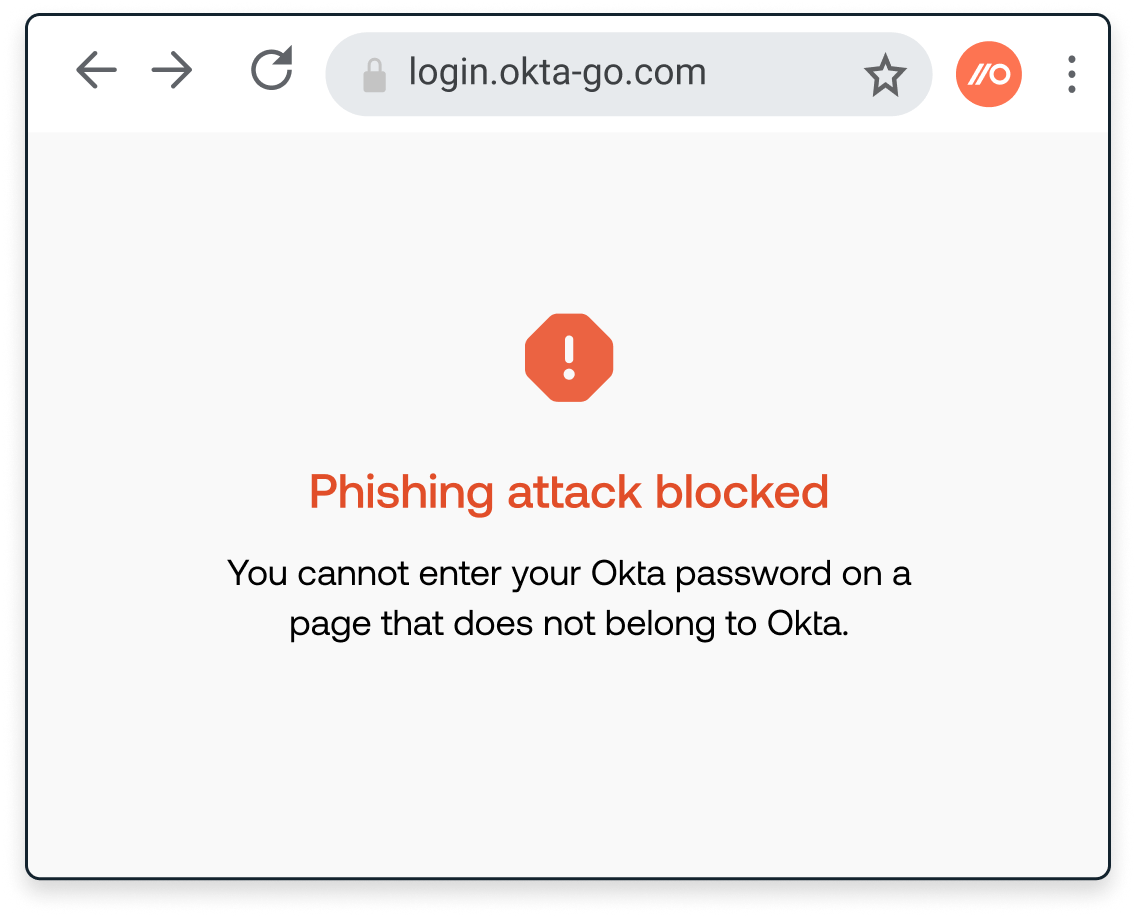
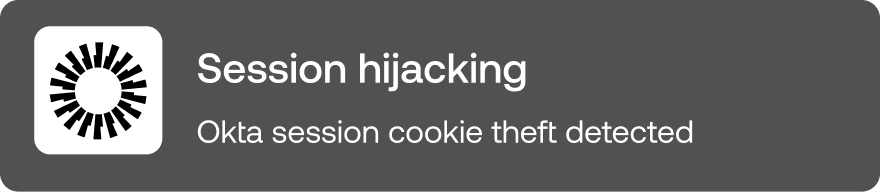
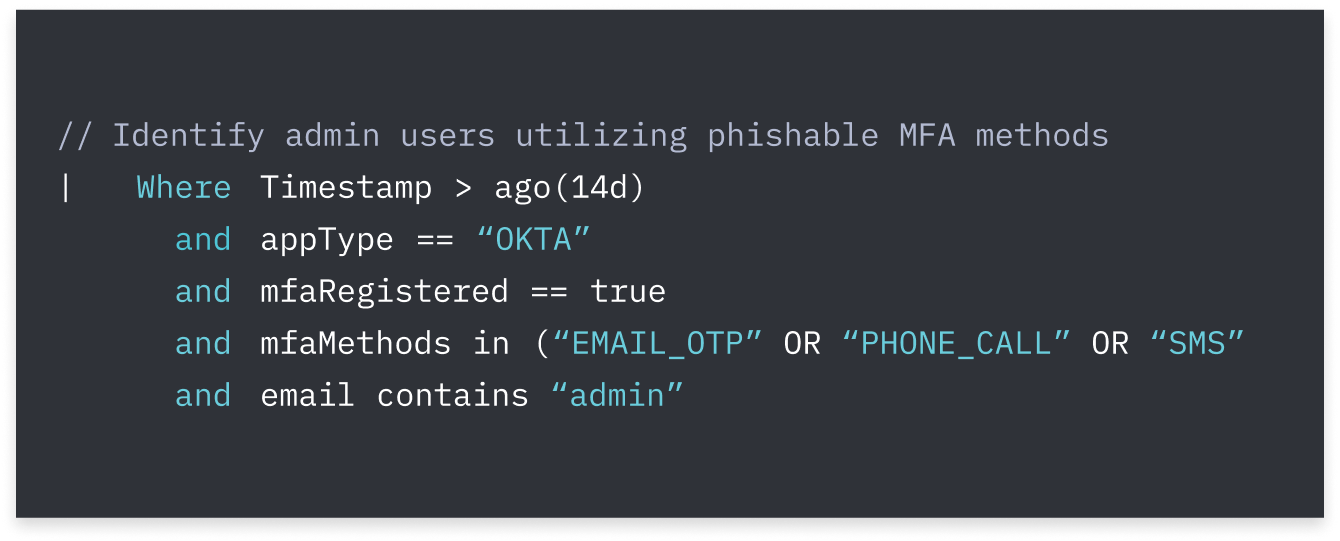
Push gives your blue team the broadest, most contextual source of telemetry for monitoring all your workforce identities, whether they're in your IdP or not.
Using this telemetry, you can detect and respond to identity attacks that can't be observed using other telemetry sources.
Not got an in-house blue team? You can still use Push to defend your identities. Enable Push’s out-of-the-box security controls so you can automatically block malicious activities in the browser as well as stop end-users introducing new identity vulnerabilities.
Push gives you proactive identity security posture management (ISPM) capabilities AND reactive identity threat detection and response (ITDR) capabilities in a single tool.
Who Uses Push Security?
SecOps teams
Not sure about Push Security?
Compare with a popular alternative

Push Security
Push Security Reviews for Indian Users
Average score
Reviews by company size (employees)
- <50
- 51-200
- 201-1,000
- >1,001
Find reviews by score
Solves Shadow IT and insecure SaaS usage by employees
Comments: Until Push, Shadow IT has been an incredibly difficult and time-consuming challenge. Push achieves this through a simple browser extension which protects employees' privacy, deploys easily and offers support to the end user through in-browser prompts.Real-time Slack notifications are sent to the employee and security team when Push detects insecure usage of a SaaS app, i.e., 2FA not applied or bad or compromised passwords being used. This helps us understand where our password manager hasn't been adopted or if the employee is having difficulty using it.The security team now receive real-time Slack notifications when new SaaS services are accessed by employees, allowing us to understand the impact and act immediately where necessary.
Pros:
Solves Shadow IT, maps the SaaS apps that can't be locked to SSO and addresses password hygiene issues (by recognising where a password manager isn't used properly) through a privacy-centric browser extension. Support team is responsive and are rapidly building in new features requested by customers.
Cons:
Push is a new product, though their support team is very responsive and addresses issues quickly.
Easy to Deploy/Maintain, Great ROI
Comments: We PoC'ed several 3rd party application security tools and ended up going with Push Security. Push was extremely easy to deploy and began providing value quickly. We were able to immediately get visibility into the SaaS and 3rd party applications in our environment as well as the strength of passwords being used. The UI/UX was really solid and the team behind the tool has a very user-centric view that resonated with us.The competitors we looked at were mostly focused on 3rd party apps, so the SaaS and password visibility was a huge differentiator for us. This allowed us to remove two dedicated security tools and save money in the end. We also found the data to be more accurate and timely in Push. For example, one competitor products reported 3rd party applications that did not exist and others failed to update the inventory quickly when applications were added or removed.
Pros:
Easy to deploy and maintain, great UI/UX, and strong integration with Slack. Additionally, Push has a very responsive and engaged team behind it.
Cons:
No cons so far - it's been very smooth sailing.
Great SaaS Discovery Product
Pros:
Push security helped us discover what SaaS was in our environment and how users were using it. The product gave additional security insights beyond just what apps were in play. It was instrumental in addressing compliance non-conformities.
Cons:
I wish there was an export button for the apps in use, for us to do further analysis. I believe its in the works.
our journey with Push Security
Comments: he made us save so much in terms of budget, I was able to terminate other SaaS application and run all those tasks using only Push Security, The best part is the fact that the people behind the application know the issue on day to day activities we face in info/cyber sec, the felt the same and what are doing is targeting those issues
Pros:
The list of integration and how easy to use is the tool, I needed something quick to deploy, fast to learn how to use and reliable.
Cons:
So far nothing, the support is amazing, able to contact directly one of the [SENSITIVE CONTENT]